Wi-Fi CERTIFIED WPA3™ December 2020 update brings new protections against active attacks: Operating Channel Validation and Beacon Protection | Wi-Fi Alliance

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

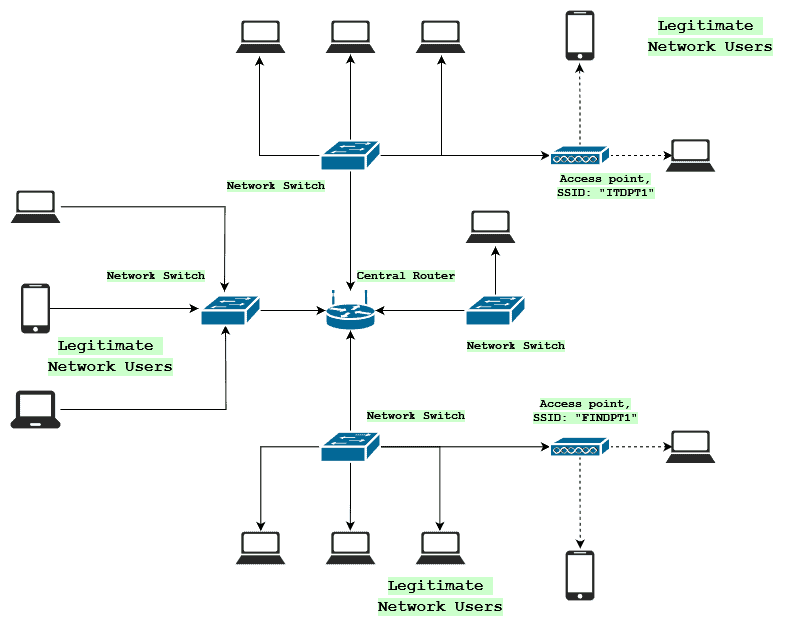
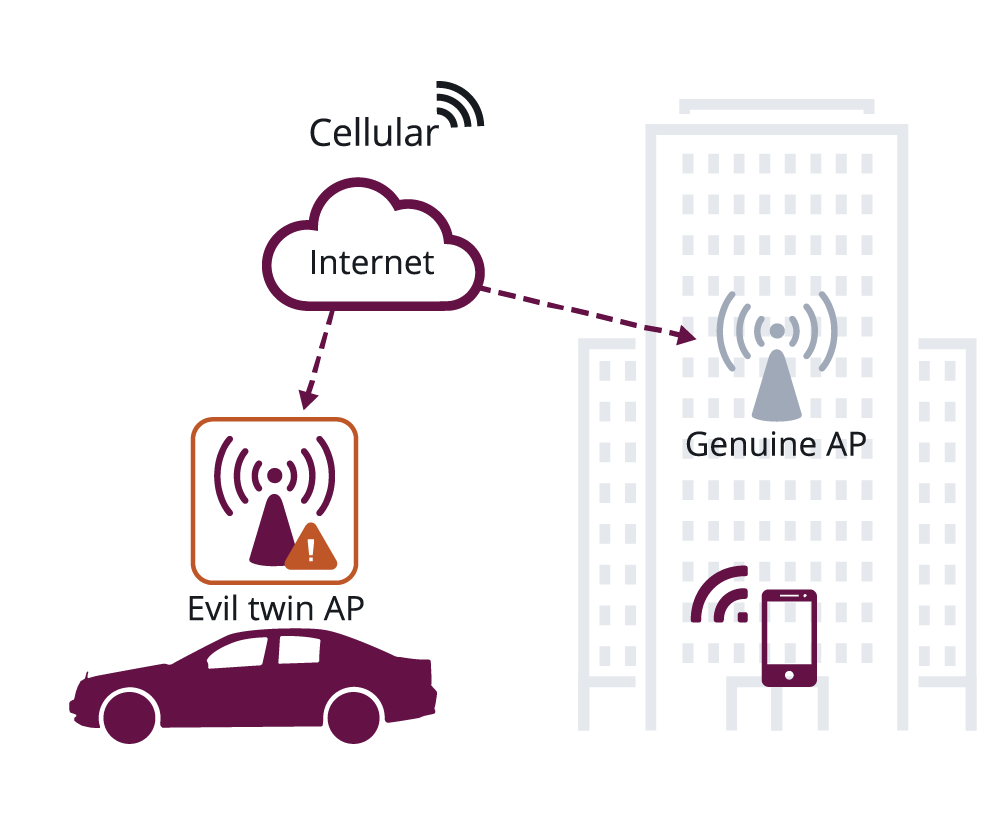
Case 4: Multiple genuine APs and multiple evil twin APs; a sub-set of... | Download Scientific Diagram

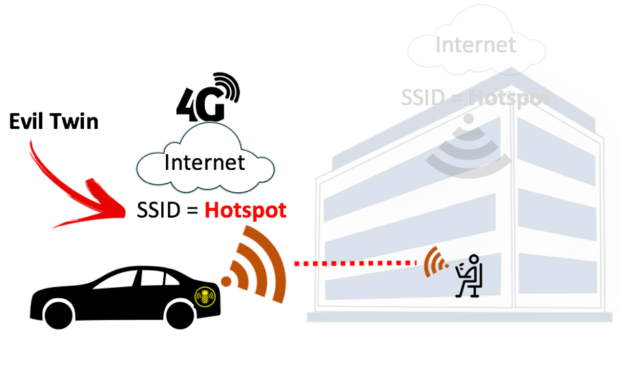
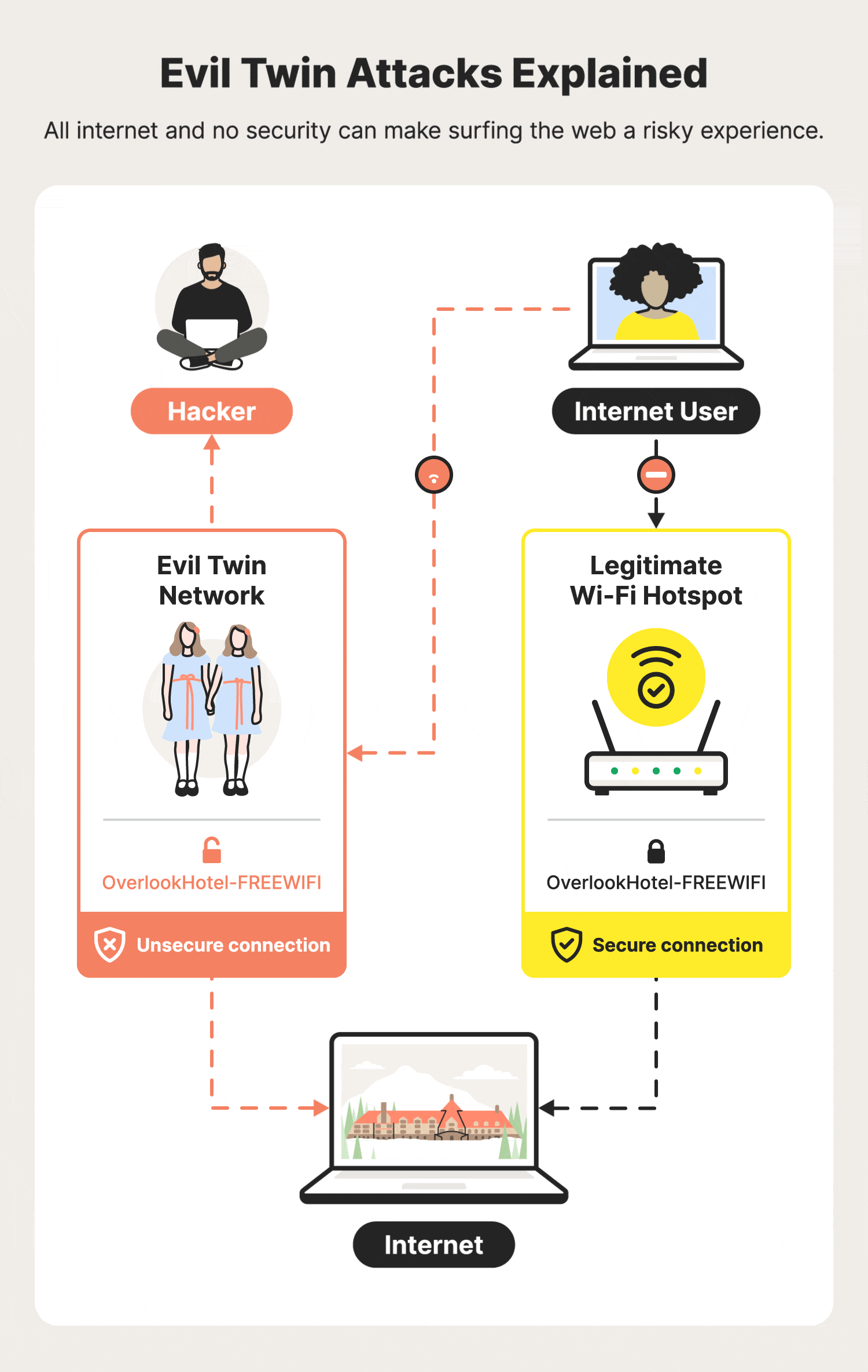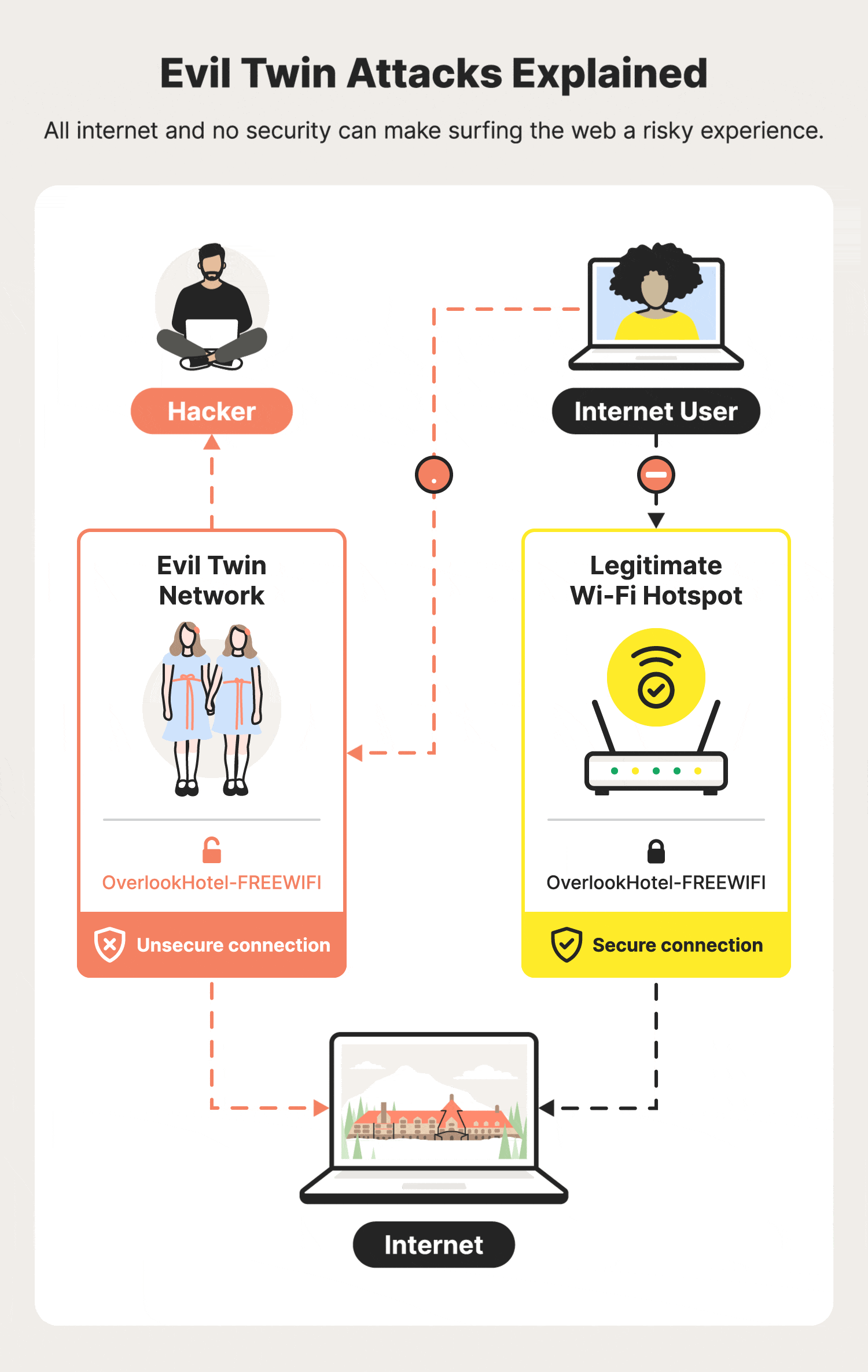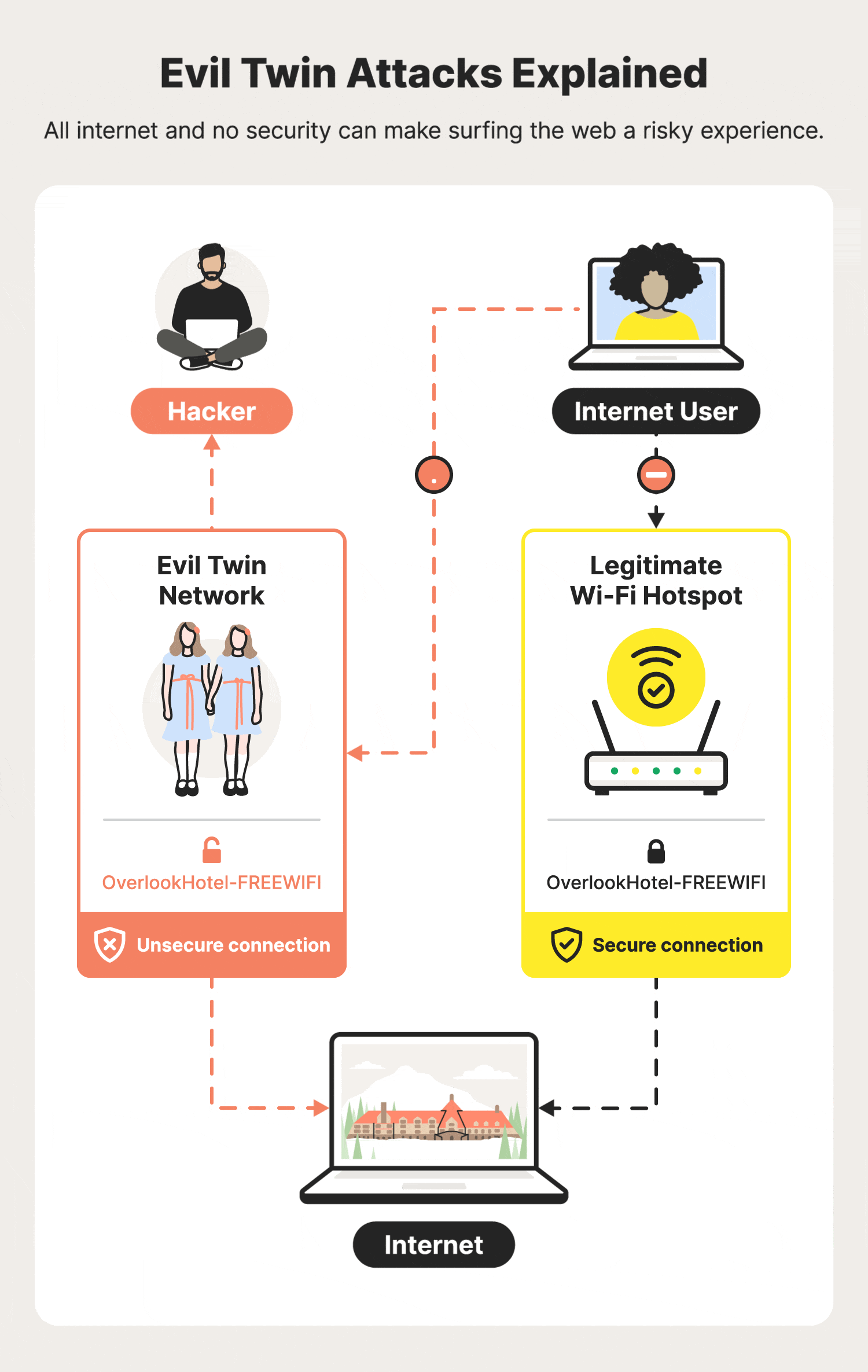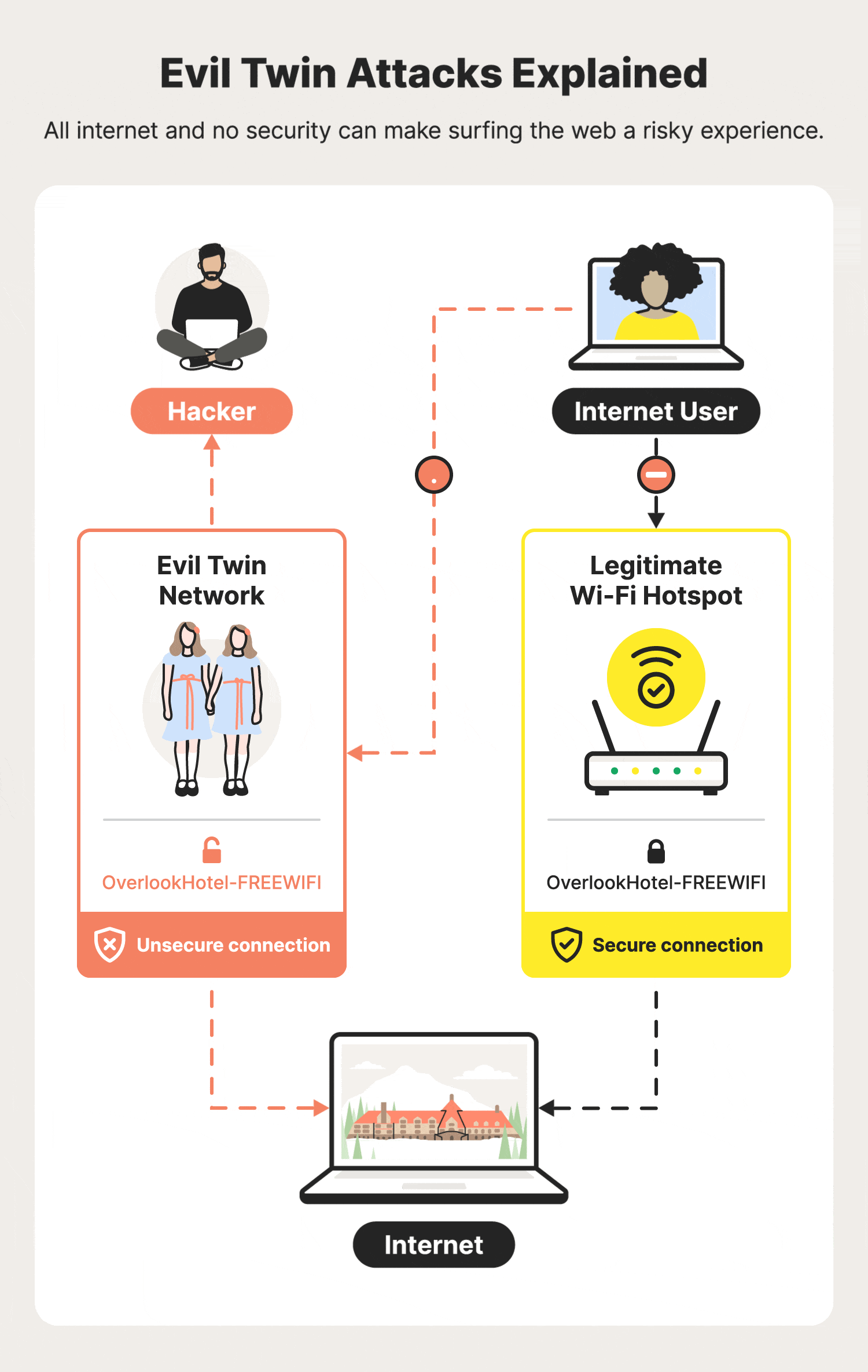
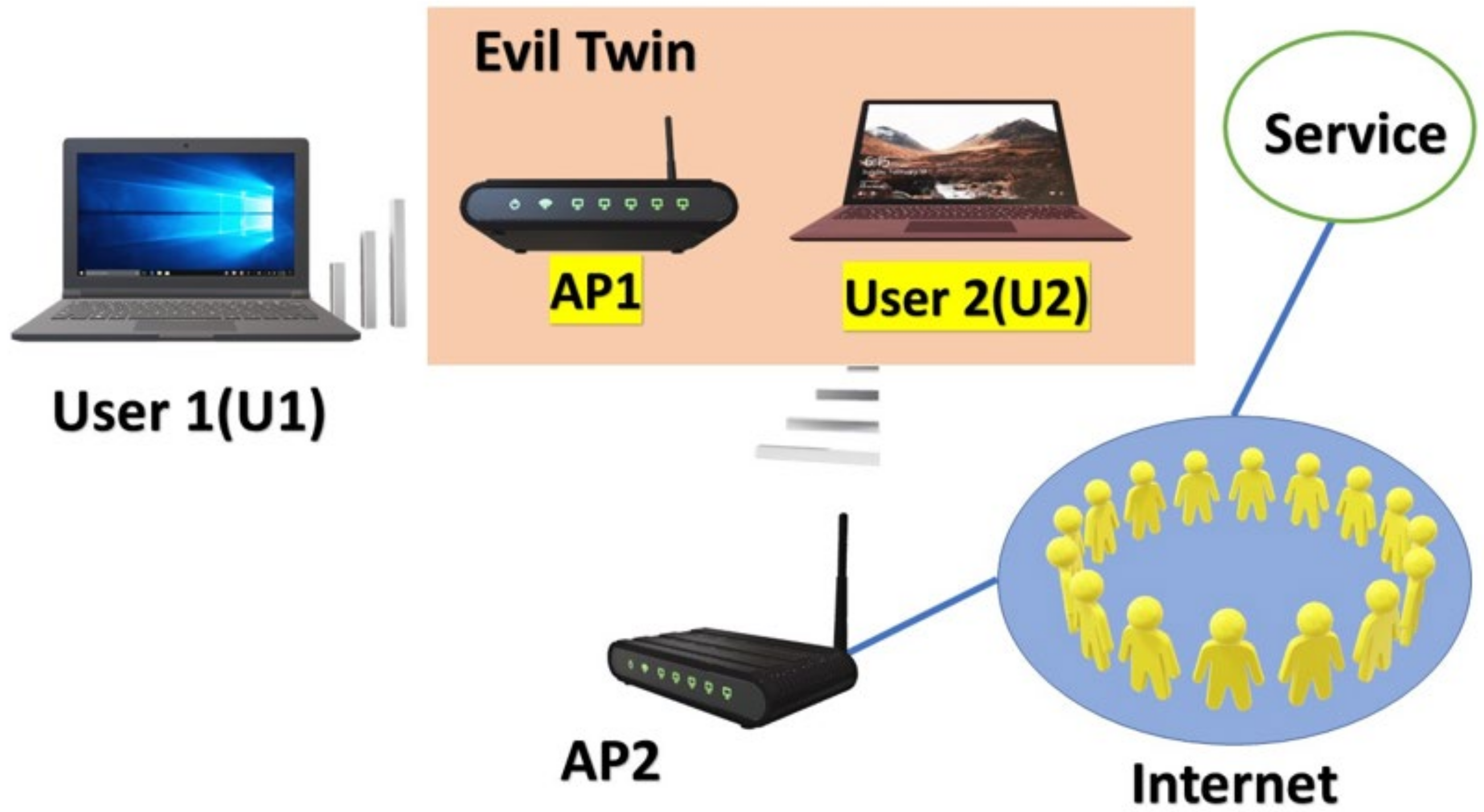
Illustration of an Evil Twin Attack. The attacker can successfully lure... | Download Scientific Diagram
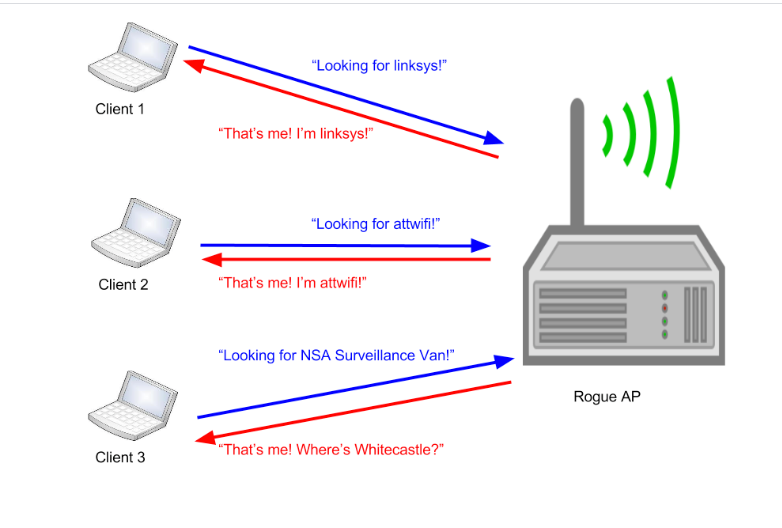
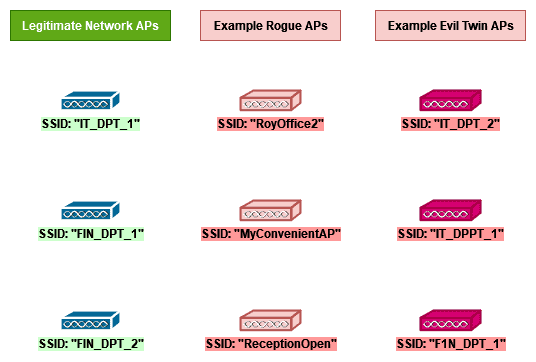
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members